LDAP
Overview
This component allows you to perform LDAP operations on directory services. You can search and retrieve information from LDAP directories. These directories are commonly used for user authentication, contact information, and organizational data.
|
This component has no trigger functions. It is not accessible to select as a first component during the integration flow design. You must use it as a subsequent component in your integration flow. |
Prerequisites
To use this component you must:
-
Have access to an LDAP directory server;
-
Know the LDAP server URL and connection details;
-
Have appropriate credentials to access the LDAP directory; and
-
Understand LDAP search filters and base DN structure
Credentials
This component requires LDAP authentication credentials to connect to your directory server.
| Field name | Mandatory | Description |
|---|---|---|
LDAP URL |
true |
The URL of your LDAP server (for example, ldap://ldap.example.com:389 or ldaps://ldap.example.com:636) |
Username |
true |
The distinguished name (DN) of the user account for LDAP authentication |
Password |
true |
The password for the LDAP user account |
|
For secure authentication, LDAPS (LDAP over SSL) on port 636 is recommended when the LDAP server is a Microsoft Active Directory Server. LDAPS is not part of the LDAP standard but is the preferred Active Directory authentication method. For other LDAP servers, STARTTLS (LDAP over TLS) on port 389 is the likely supported authentication method. Check with your LDAP server vendor before implementation, however. Connecting to the LDAP server in the clear on port 389 is also technically supported by this component. This connection method is not recommended. There are enormous security risks sending user data, and especially user authentication data, as PLAINTEXT. |
Usage
The LDAP component is used to search directory information. You can search for users, groups, or any other objects stored in your LDAP directory.
-
Configure your LDAP credentials with the server URL, username, and password
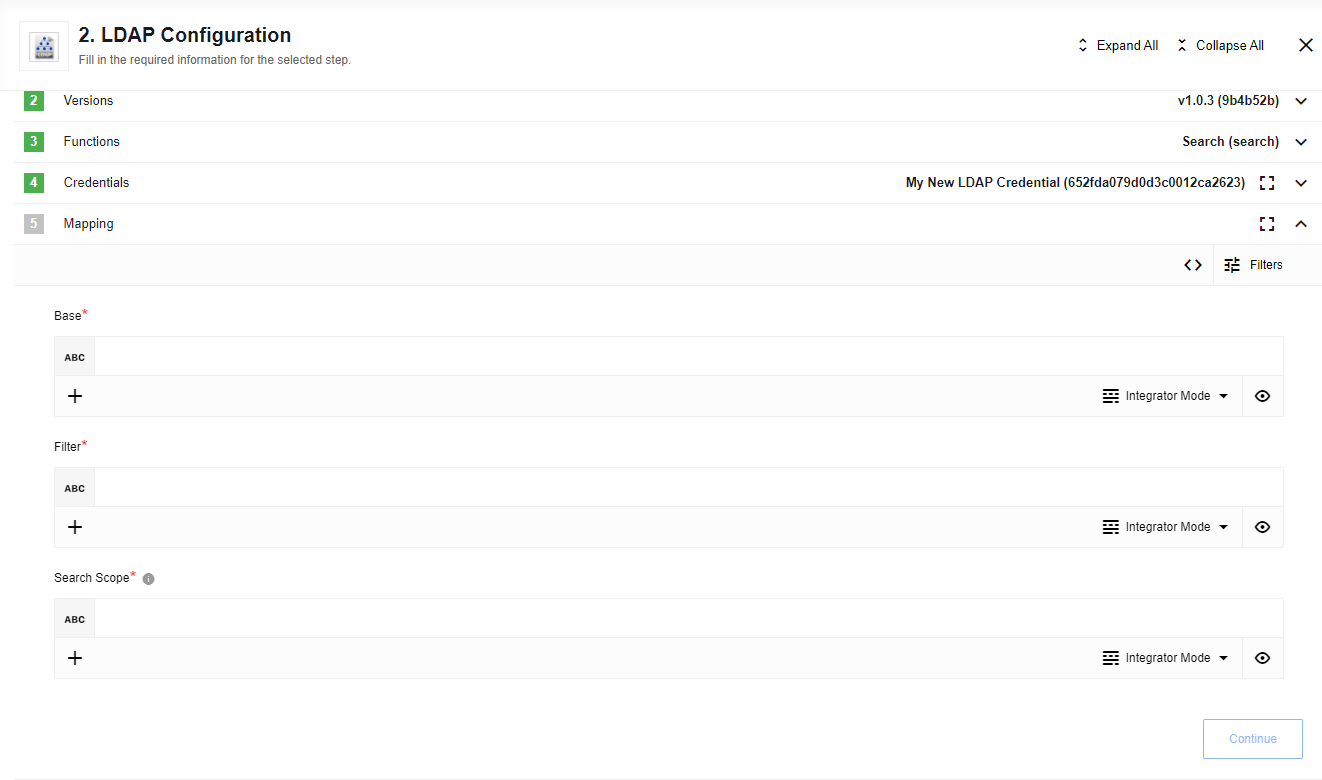
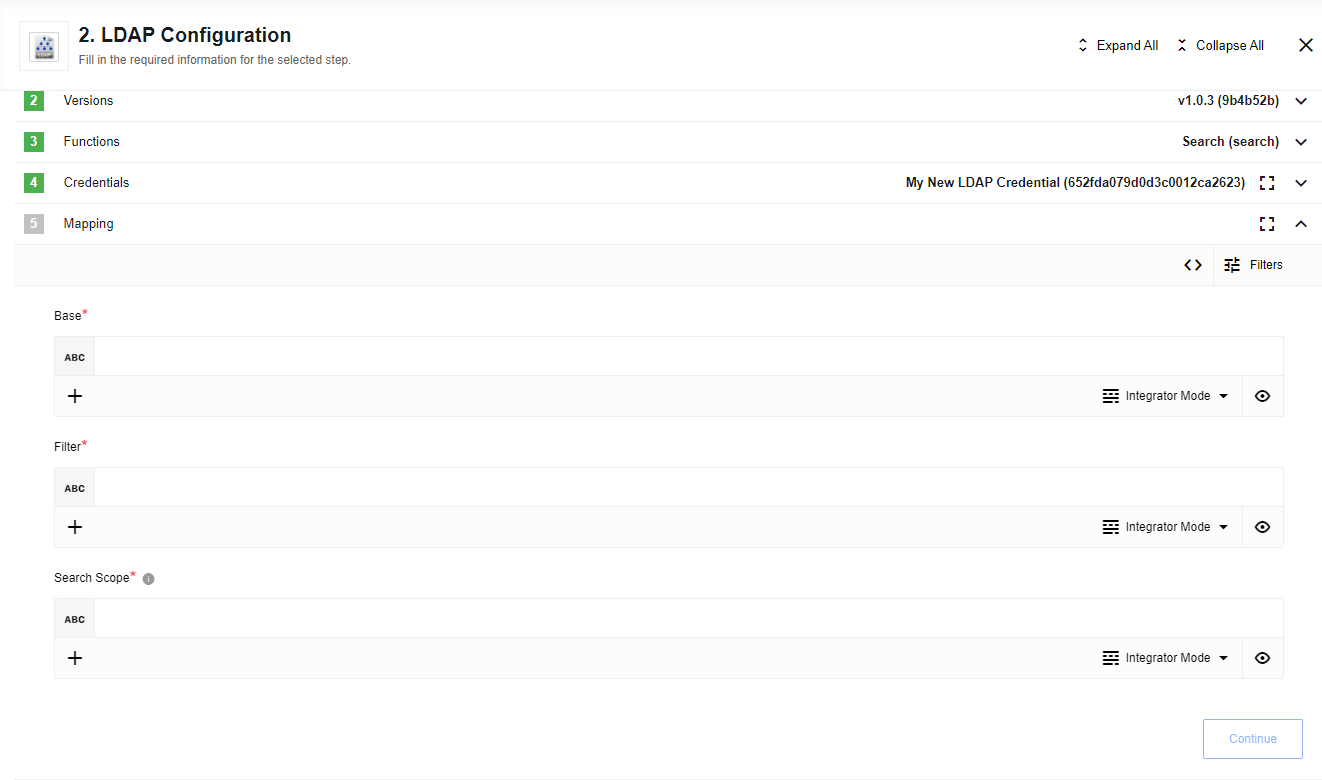 Figure 1. LDAP component configuration form showing URL, username, and password fields
Figure 1. LDAP component configuration form showing URL, username, and password fields -
Set up the search action with your desired base DN, filter, and scope
-
Execute the search to retrieve directory information
-
Process the returned LDAP entries in your integration flow
Actions
This component has one action.
Search
Performs an LDAP search operation on the instance to retrieve directory information.
Input metadata
- Base
-
A required string field.
The base object in the directory from which to start the search. This is typically the root DN of your directory structure (for example, "dc=example,dc=com").
- Filter
-
A required string field.
Allows you to specify one or more LDAP filters to restrict the results of the search.
Common filters include the following:
(objectClass=person)::: Find all person objects(uid=username)::: Find a specific user by UID(cn=John)::: Find entries with common name containing "John" - Scope
-
A required string field.
Refers to the search scope. Options are:
base::: Search only the base object itselfone::: Search one level below the base objectsub::: Search the entire subtree below the base object
|
The |
Output metadata
The output metadata includes the LDAP search results with the following structure:
{
"dn": "distinguished name of the entry",
"attributes": {
"attributeName": ["attribute values"],
"cn": ["Common Name"],
"uid": ["user identifier"],
"mail": ["email@example.com"]
}
}Usage example
LDAP server: ldap://ldap.example.com:389 Base DN: dc=example,dc=com
{
"base": "dc=example,dc=com",
"filter": "(objectClass=person)",
"scope": "sub"
}{
"dn": "uid=john.doe,ou=people,dc=example,dc=com",
"attributes": {
"uid": ["john.doe"],
"cn": ["John Doe"],
"mail": ["john.doe@example.com"],
"objectClass": ["top", "person", "organizationalPerson", "inetOrgPerson"]
}
}Limitations
The limitations of this component are as follows:
-
The
subordinates(also known assubordinateSubtree) scope is not supported; -
Only LDAP v3 is supported;
-
No trigger functions are available;
-
Search results are returned individually for each matched entry; and
-
Complex LDAP filters may impact performance
Authentication
Authentication is via LDAP bind using username (DN) and password credentials.
SASL authentication is not supported.
Setting credentials
To set the required credentials:
-
Open the component configuration panel in your integration flow;
-
Enter your LDAP server URL (use ldaps:// for secure connections);
-
Provide the distinguished name (DN) of your LDAP user account;
-
Enter the password for the LDAP user account; and
-
Test the connection to verify credentials are correct.
|
Ensure your LDAP user account has read permissions for the directory structure you need to access. |