Personally identifiable information (PII) in Logs
The Squiz DXP Logging Service is a centralized logging solution for other Squiz DXP services.
It may contain sensitive information requiring careful handling to ensure compliance with privacy regulations and protect user data.
Logs may contain sensitive information. Always treat log data as potentially sensitive and handle it according to your organization’s privacy policies.
|
Matrix and Funnelback logs are not available in the DXP Logs service. For these logs, use the Matrix Log Manager or refer to the Funnelback Logs reference. |
What is PII?
Personally identifiable information (PII) in logs refers to any information that can be used to identify an individual person.
This includes:
- Direct identifiers
-
Names, email addresses, phone numbers, social security numbers.
- Indirect identifiers
-
IP addresses, user IDs, session tokens, device identifiers.
- Contextual information
-
Location data, timestamps combined with user actions.
- Behavioral data
-
User interactions, form submissions, search queries.
Access control for PII in logs
The Logging Service contains sensitive information that requires appropriate access controls.
- Primary roles
-
Users with Owner, Admin, or Developer primary roles have access to the Logging Service.
- Secondary roles
-
Users with the Logs Auditor secondary role can view sensitive information in the Logging Service, including PII that is masked by default.
For detailed information about the Logs Auditor role, including assignment procedures and security considerations, see Logs Auditor secondary role.
PII auditing feature in the Logging Service
To address the need for authorized users to view specific obfuscated data for auditing purposes, the Logging Service includes a PII auditing feature.
PII strings are masked by default and appear to all users as PII-HIDDEN (in italics).
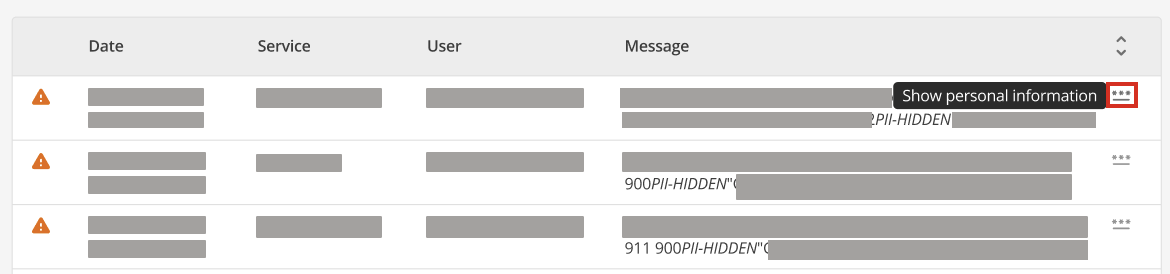
A toggle to show PII is available to users with the Logs Auditor secondary role. When the toggle is clicked, two things happen:
-
The log entry re-loads inline (after loading), showing the PII plainly;
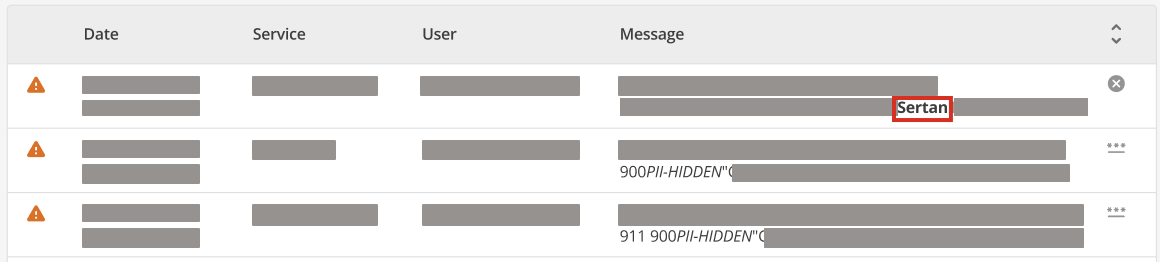 Figure 2. A log sample showing the PII view enabled.
Figure 2. A log sample showing the PII view enabled. -
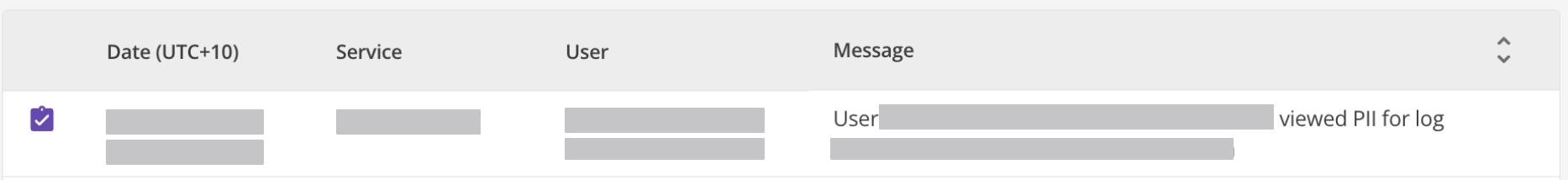
A new log entry is created to record the fact that the PII was revealed, and by whom.
The PII can be hidden again by using the same toggle, or it will be automatically re-masked when you refresh the log results or perform a new search.
|
This happens at the level of a single log message. To view multiple messages' worth of PII, each individual row must be clicked. This is designed to be more secure and to make logging the audit message easier. |
PII audit logs
When PII is revealed using the toggle, a new audit log entry is created and appears in the standard Logging Service interface. These audit logs:
-
Are stored as audit log type (one of the four log types: info, audit, warning, or error).
-
Include details about who revealed the PII and when.
-
Can be viewed by anyone who has access to the Logging Service.
-
Are retained according to the standard audit log retention policy (12 months in hot storage).
This provides a complete audit trail for compliance and security monitoring purposes.
When this toggle is used, logs are generated to know who has requested the data.
This provides a vital audit trail for PII access.
The PII toggle, once enabled, will show all information from the Message and User ID columns that was previously obfuscated.
How to view PII in logs
If you have the Logs Auditor secondary role, you can temporarily reveal masked PII in log entries for legitimate auditing and compliance purposes.
Before you start
-
Ensure you have been assigned the Logs Auditor secondary role by an Owner.
-
Understand your organization’s policies for handling PII.
-
Have a legitimate business need to view the sensitive information.
-
Be aware that each time you reveal PII, an audit log entry is created.
Steps
To view PII in log entries:
-
Navigate to the Logs service in your Squiz DXP Console at .
-
Use the filtering tools to narrow down the log entries you need to examine.
-
Use date and time filters to focus on a specific period
-
Filter by service name if you know which service generated the logs
-
Use keyword search to find specific log entries
-
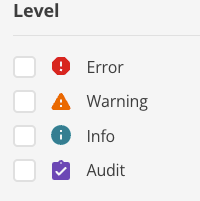
Filter by log level (Info, Warning, Error, or Audit) as needed
-
-
Look for log entries that contain
PII-HIDDENin the Message column.These entries contain masked PII that you can reveal if needed.
-
Click the
⋯icon to the right of the log entry. -
Select Show personal information.
The log entry will reload inline, revealing the previously masked PII data.
-
Review the revealed information as needed for your audit or compliance task.
-
To hide the PII again, use the same toggle, refresh the page, or perform a new search.
Viewing PII audit logs
To review who has accessed PII:
-
In the Logs service, filter by log level and select Audit.
This shows all audit log entries, including PII access events.
-
Look for audit log entries related to PII access.
These entries will indicate which user revealed PII and when.
-
Use the date range filter to focus on specific time periods if needed.
Best practices for handling PII in logs
To ensure proper handling of PII within the Logging Service, consider the following best practices:
- Access control
-
-
Only grant access to users who have a legitimate business need.
-
Use the Logs Auditor secondary role for users who need to view sensitive log information.
-
Regularly review and audit access permissions.
-
- Data handling
-
-
Minimize the collection of PII in logs.
-
Use secure methods when sharing or exporting log data.
-
Use data anonymization or pseudonymization for long-term log storage.
-
- Compliance considerations
-
-
Ensure log handling practices comply with relevant privacy regulations (GDPR, CCPA).
-
Document your organization’s approach to PII in logs.
-
Establish procedures for responding to data subject requests.
-
Follow any right to be forgotten and data deletion requirements.
-
- Security considerations
-
-
Only reveal PII when you have a legitimate business need.
-
PII access is logged for audit purposes.
-
Each log entry must be revealed individually - there’s no bulk reveal option.
-
PII is automatically re-masked when log results are refreshed.
-
Follow your organization’s data protection policies.
-
Data retention policies
-
Regular logs (Info, Error, Warning) are kept for 30 days.
The UI updates include the ability to show 30 days of logs.
-
Hot storage of audit logs is for 12 months.
-
Cold storage is used for inactive audit logs.
-
Establish clear retention periods for log data containing PII and implement automated deletion processes where possible.
-
Document your retention policies and procedures, considering legal and regulatory requirements.